Here are 9 Salesforce best practices that will help organizations avoid potentially catastrophic data loss events:

RELATED BLOG POSTS
Setting Up and Using CodeScan Effectively
Running CodeScan on your Salesforce Org is a great first step towards quality code, but maintaining that quality is a Read more
Estimating ROI with CodeScan
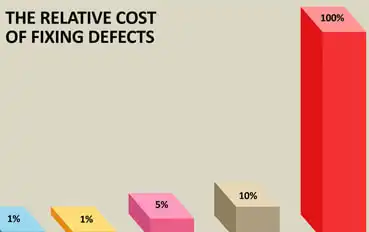
Every Software Development Professional knows the following fact: the later bugs are found, the more expensive they are to fix. Read more
SFDX Tutorial | Setting Up CodeScan
Salesforce DX is a new focus on source-driven, collaborative development. The Salesforce CLI (Command Line Interface) easily integrates into your Read more
CodeScan and Visual Studio Team Services
Visual Studio Continuous IntegrationVisual Studio Team Services (VSTS) is a quick and powerful tool to set up continuous integration and Read more

 Salesforce best practices provide a road map to secure behaviors that will help teams avoid data security issues when uniformly followed.
Salesforce best practices provide a road map to secure behaviors that will help teams avoid data security issues when uniformly followed.
 We mentioned the unavoidability of human error. This vulnerability can be addressed in multiple ways, one of which is to make use of automated DevSecOps tools whenever possible. Taking time-consuming, repetitive tasks out of the hands of your team members speeds along projects, reduces errors, and enables your team to focus on more pressing matters.
We mentioned the unavoidability of human error. This vulnerability can be addressed in multiple ways, one of which is to make use of automated DevSecOps tools whenever possible. Taking time-consuming, repetitive tasks out of the hands of your team members speeds along projects, reduces errors, and enables your team to focus on more pressing matters. The code that makes up your updates and applications can either support or hinder your data security strategy. Bad code creates misfires and buggy applications while strong code forms an impenetrable barrier against
The code that makes up your updates and applications can either support or hinder your data security strategy. Bad code creates misfires and buggy applications while strong code forms an impenetrable barrier against