Here are 10 common Salesforce vulnerabilities that need prevented to remain secure:

RELATED BLOG POSTS
Setting Up and Using CodeScan Effectively
Running CodeScan on your Salesforce Org is a great first step towards quality code, but maintaining that quality is a Read more
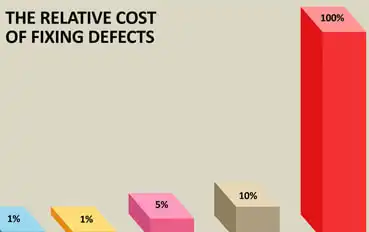
Estimating ROI with CodeScan
Every Software Development Professional knows the following fact: the later bugs are found, the more expensive they are to fix. Read more
SFDX Tutorial | Setting Up CodeScan
Salesforce DX is a new focus on source-driven, collaborative development. The Salesforce CLI (Command Line Interface) easily integrates into your Read more
CodeScan and Visual Studio Team Services
Visual Studio Continuous IntegrationVisual Studio Team Services (VSTS) is a quick and powerful tool to set up continuous integration and Read more

 Being aware of Salesforce vulnerabilities makes it much more likely your team can successfully prevent them.
Being aware of Salesforce vulnerabilities makes it much more likely your team can successfully prevent them.
 Cross-site scripting (XSS) is a security vulnerability in Salesforce that allows attackers to inject malicious scripts into webpages, applications, and platforms. Within Salesforce Visualforce pages, an unescaped value has the potential to become a vector for an XSS attack.
Cross-site scripting (XSS) is a security vulnerability in Salesforce that allows attackers to inject malicious scripts into webpages, applications, and platforms. Within Salesforce Visualforce pages, an unescaped value has the potential to become a vector for an XSS attack.
 Access screens are still one of the first potential entry points targeted by cybercriminals. Why go through the trouble of hacking into a system when you can simply enter a username and password? These credentials can be compromised through phishing attempts, weak passwords, and exposed information.
Access screens are still one of the first potential entry points targeted by cybercriminals. Why go through the trouble of hacking into a system when you can simply enter a username and password? These credentials can be compromised through phishing attempts, weak passwords, and exposed information.