Here are 8 ways Salesforce monitoring tools protect your system data:

RELATED BLOG POSTS
Setting Up and Using CodeScan Effectively
Running CodeScan on your Salesforce Org is a great first step towards quality code, but maintaining that quality is a Read more
Estimating ROI with CodeScan
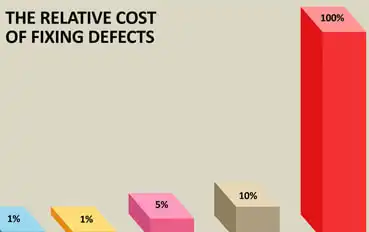
Every Software Development Professional knows the following fact: the later bugs are found, the more expensive they are to fix. Read more
SFDX Tutorial | Setting Up CodeScan
Salesforce DX is a new focus on source-driven, collaborative development. The Salesforce CLI (Command Line Interface) easily integrates into your Read more
CodeScan and Visual Studio Team Services
Visual Studio Continuous IntegrationVisual Studio Team Services (VSTS) is a quick and powerful tool to set up continuous integration and Read more

 Visibility into your DevOps pipeline helps prevent and address data security risks. Salesforce monitoring tools provide the support you need to accomplish this.
Visibility into your DevOps pipeline helps prevent and address data security risks. Salesforce monitoring tools provide the support you need to accomplish this.
 Data protection requires immediacy. This isn’t something you can sit on for a while and eventually get to when you have some spare time. Any delay could mean the difference between preventing data loss and experiencing a costly outage. Data security threats are occurring around the clock to exploit vulnerabilities. You need to be ready to act at any time.
Data protection requires immediacy. This isn’t something you can sit on for a while and eventually get to when you have some spare time. Any delay could mean the difference between preventing data loss and experiencing a costly outage. Data security threats are occurring around the clock to exploit vulnerabilities. You need to be ready to act at any time. Planning and adjusting your strategy are huge aspects of maintaining a successful Salesforce data security strategy over time. Cybercriminals are always looking for new ways to find and exploit vulnerabilities—your response must be equally diligent. And the most effective way to do this is to analyze metrics for clues on how to make the correct adjustments.
Planning and adjusting your strategy are huge aspects of maintaining a successful Salesforce data security strategy over time. Cybercriminals are always looking for new ways to find and exploit vulnerabilities—your response must be equally diligent. And the most effective way to do this is to analyze metrics for clues on how to make the correct adjustments.