Here are five things you need to know about Salesforce vulnerabilities and your responsibilities related to them:

RELATED BLOG POSTS
Setting Up and Using CodeScan Effectively
Running CodeScan on your Salesforce Org is a great first step towards quality code, but maintaining that quality is a Read more
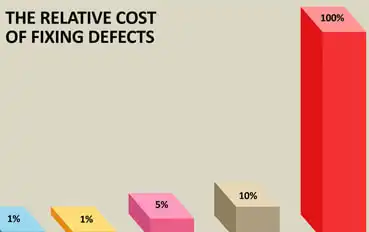
Estimating ROI with CodeScan
Every Software Development Professional knows the following fact: the later bugs are found, the more expensive they are to fix. Read more
SFDX Tutorial | Setting Up CodeScan
Salesforce DX is a new focus on source-driven, collaborative development. The Salesforce CLI (Command Line Interface) easily integrates into your Read more
CodeScan and Visual Studio Team Services
Visual Studio Continuous IntegrationVisual Studio Team Services (VSTS) is a quick and powerful tool to set up continuous integration and Read more

 Every Salesforce user is responsible for securing their own environment. This includes accounting for Salesforce vulnerabilities.
Every Salesforce user is responsible for securing their own environment. This includes accounting for Salesforce vulnerabilities.
 Working outside the Salesforce platform clears up a lot of confusion about where responsibility falls for data security considerations. When it comes to DevOps, most environments exist directly within the Salesforce platform. And while this might seem like an advantage, it opens organizations up to outages—both planned and unplanned—from Salesforce itself.
Working outside the Salesforce platform clears up a lot of confusion about where responsibility falls for data security considerations. When it comes to DevOps, most environments exist directly within the Salesforce platform. And while this might seem like an advantage, it opens organizations up to outages—both planned and unplanned—from Salesforce itself.