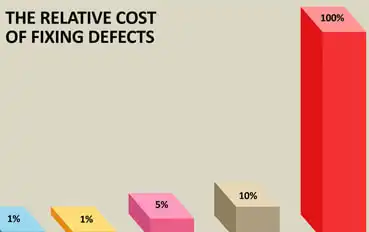
Why It Matters: You can’t expect team members to catch everything, but even a small error can have huge ramifications on the overall security and compliance of your Salesforce environment.
- Bugs and errors in live applications can create back doors for cybercriminals.
- A recent report from Gartner predicts that 45% of organizations globally will have experienced an attack on their software supply chain by 2025.
- Automated Salesforce security scans offer wide coverage and reliable results when performed correctly.