Here are 9 Salesforce vulnerabilities that can be addressed with automated DevSecOps tools:

RELATED BLOG POSTS
Setting Up and Using CodeScan Effectively
Running CodeScan on your Salesforce Org is a great first step towards quality code, but maintaining that quality is a Read more
Estimating ROI with CodeScan
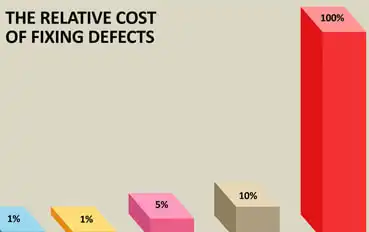
Every Software Development Professional knows the following fact: the later bugs are found, the more expensive they are to fix. Read more
SFDX Tutorial | Setting Up CodeScan
Salesforce DX is a new focus on source-driven, collaborative development. The Salesforce CLI (Command Line Interface) easily integrates into your Read more
CodeScan and Visual Studio Team Services
Visual Studio Continuous IntegrationVisual Studio Team Services (VSTS) is a quick and powerful tool to set up continuous integration and Read more

 Integrate automated tools to address Salesforce vulnerabilities and protect critical system data.
Integrate automated tools to address Salesforce vulnerabilities and protect critical system data.
 Permission sets work alongside profiles to grant users access to types of data. In Salesforce, administrators can grant multiple permission sets to a particular profile to customize the data they are able to access. However, this can create conflicts and lead to someone having access to data they don’t need to perform their duties.
Permission sets work alongside profiles to grant users access to types of data. In Salesforce, administrators can grant multiple permission sets to a particular profile to customize the data they are able to access. However, this can create conflicts and lead to someone having access to data they don’t need to perform their duties. Protecting your Salesforce environment isn’t always as straightforward as it might seem. Unauthorized individuals can gain access to system records without giant alarms going off. In fact, it takes
Protecting your Salesforce environment isn’t always as straightforward as it might seem. Unauthorized individuals can gain access to system records without giant alarms going off. In fact, it takes